Microsoft Defender for Office 365
Office 365 workloads come with protection capabilities by default, mainly Exchange Online Protection (EOP). For a quick refresh, EOP provides Exchange Online admins with inbound and outbound anti-spam policies, antimalware protection, message quarantining, message tracing, zero-hour purging configurations, and more. While these capabilities are imperative to protect organizations with constant email exchanges, EOP focuses more on preventative measures.
Microsoft Defender for Office 365(MDO) extends EOP’s protection capabilities by providing detection, investigation, and response capabilities. MDO used to be called Office 365 Advanced Threat Detection.
Like MDE, MDO also has two tiers: MDO P1 and MDO P2. On top of EOP’s capabilities, MDO P1 adds more protection features, such as safe attachments and safe links, and security protection that extends to other Office 365 workloads, such as SharePoint Online and Teams. Additionally, P1 offers more investigation capabilities, such as API integrations for SIEM tools and real-time detection tools. Further, P2 adds more investigation and response features, including threat explorer and automated investigation and response (AIR). MDO P1 is included with EMS E3 and includes the Safe Linksand Safe Attachments features, which evaluate content and links in a sandbox for threats.
Defender for Office 365 P2, included with EMS E5, expands that protection with end user-focused threat training campaigns, the threat explorer, and AIR capabilities.
MDO P1 and P2
The service description page provides a comprehensive list of the features available in P1 versus P2. It is important to know these, so visit https://learn.microsoft.com/ en-us/office365/servicedescriptions/office-365-advanced-threat-protection-service-description#feature-availability.
As described earlier, email can be a common starting point for an attack. To leverage MDO effectively, start with configuring some of the core email security features, such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) records. You should also consider setting up Authenticated Received Chain (ARC) senders for the organization’s domains.
Further Reading
The exact configuration of SPF, DKIM, DMARC, and ARC are outside the scope of the MS-900 exam. You can learn more about each of these email protection technologies at: https:// learn.microsoft.com/en-us/microsoft-365/security/office-365-security/email-authentication-about.
These records help protect against spoofing. Setting up such authentication makes it harder for attackers to use your domain for their attack campaigns. Then, continue the MDO deployment by configuring the security features provided by the elevated plans. IT admins can get started with MDO by either going with the recommended pre- set policies or manually configuring them. Policies to configure manually include antimalware, safe links, safe attachments, as well as protections that extend to Office 365 workloads.
These policies can be found in the Defender portal. To get there, follow these steps:
- Navigate to https://security.microsoft.com.
- Expand Email & collaboration.
- Choose Policies & rules.
- Click on Threat policies, which opens up a page as shown in Figure 9.11:
Figure 9.11 – Microsoft Defender for Office Threat policies page
When selecting the recommended, pre- set route, there are two security levels – Standard and Strict – with the latter being slightly more aggressive than the former, the baseline.
Recommended EOP and MDO security policies
Microsoft recommends customers to start with the pre-set security policies. This page,https:// learn.microsoft.com/en-us/microsoft-365/security/office-365-
security/recommended-settings-for-eop-and-office365?view=o365-worldwide, lists out the settings for standard and strict levels.
Once MDO has been configured, security analysts can use the Microsoft 365 Defender portal to conduct their daily operations. In the portal, there are activities to complete on a regular basis, such as reviewing incident queues, managing malware, and phishing campaigns as well as proactively hunting for threats within the Office 365 environment. Don’t forget the recommended actions per Secure Score, as shown in Figure 9.12:
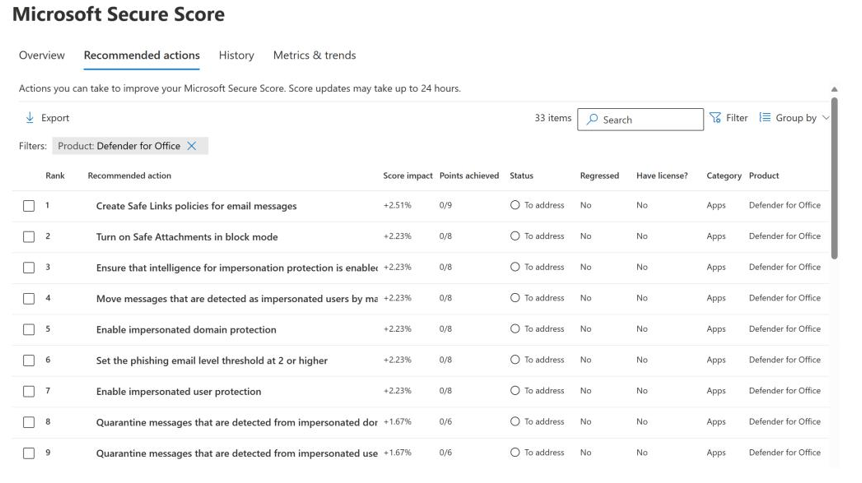
Figure 9.12 – Secure Score’s recommended actions for MDO
Mailboxes and files tie back to identity. Attackers may target a specific user’s mailbox, so Microsoft 365 Defender also protects identity. This is where Microsoft Defender for Identity can be helpful.

