Microsoft Defender for Endpoint
Microsoft Defender for Endpoint(MDE) plays a critical role in protecting users’ workstations and servers. When enabled and onboarded, the MDE service will provide prevention, detection, investigation, and response mechanisms through antivirus and antimalware protection and other advanced threat protection capabilities with management and reporting features. Microsoft recommends using Microsoft Defender Antivirus and MDE together.
In fact, Defender may suggest this as part of its recommended actions for security admins to take to improve the score, as shown in Figure 9.8:
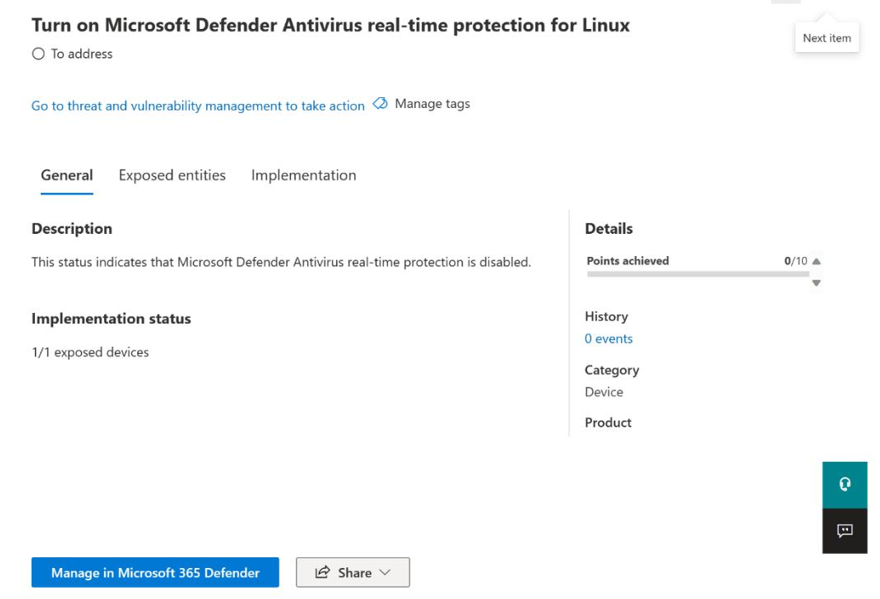
Figure 9.8 – Secure Score recommended action for MDE
Advantages when using Defender Antivirus and Defender for Endpoint together
There are many third-party antivirus software on the market today. One of these is Microsoft’s own antivirus, Microsoft Defender Antivirus. While it is not a requirement to use Microsoft Defender Antivirus, it is recommended to use Microsoft’s antivirus solution and MDE together. To understand the advantages, please visit https://learn.microsoft.com/en-us/ microsoft-365/security/defender-endpoint/why-use-microsoft-defender-antivirus?view=o365-worldwide#11-reasons-to-use-microsoft-defender-antivirus-together-with-microsoft-defender-for-endpoint.
The capabilities for MDE will depend on the licensing: MDE Plan 1 (P1) or MDE Plan 2 (P2). P2 consists of its own set of capabilities and includes all of those in P1. Table 9.1 captures the features based on the plan:
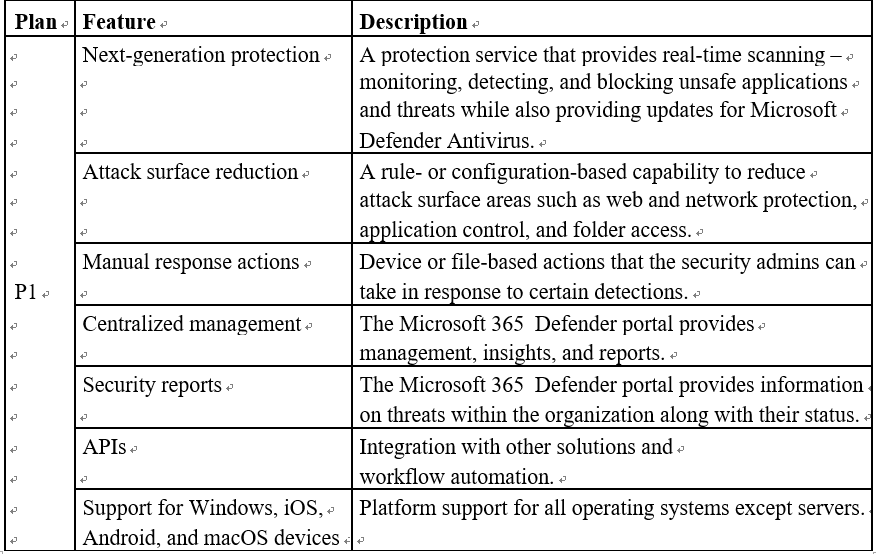
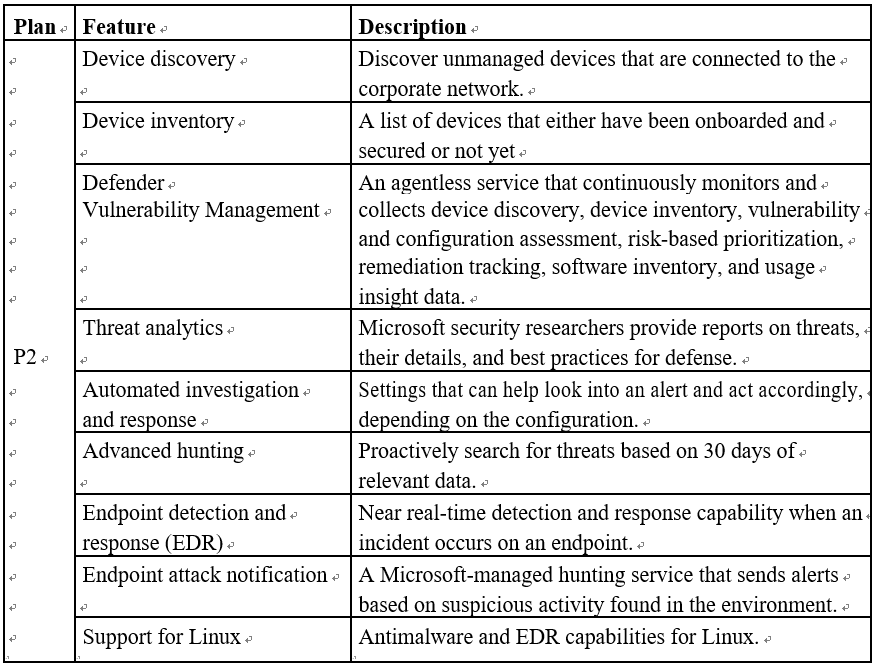
Table 9.1 – Microsoft Defender for Endpoint P1 and P2 feature table
MDE uses Microsoft Defender Vulnerability Management(MDVM) as part of its services. MDVM helps with asset visibility, vulnerability assessment, continuous monitoring, and more. Customers can choose to purchase the MDVM add-on on top of MDE P2 to get features such as security baseline and hardware and software assessments and network share analysis.
Microsoft Defender Vulnerability Management features
To learn more about what is included in MDE P2, and what is available as a separate add-on, please see https://learn.microsoft.com/en-us/microsoft-365/security/ defender-vulnerability-management/defender-vulnerability-management-capabilities?view=o365-worldwide.
To onboard endpoints and devices to MDE, IT admins have many options such as Configuration Manager, group policies, or local scripts. The Defender portal will also provide a Device inventory page, as shown in Figure 9.9.
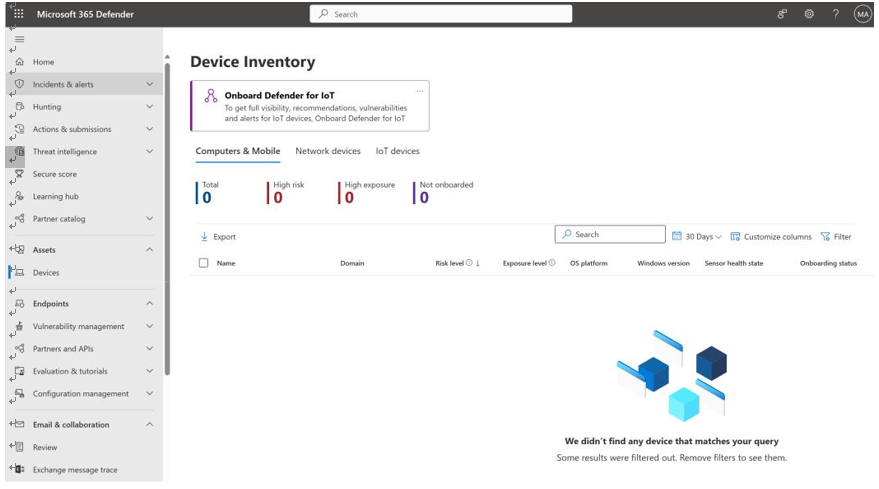
Figure 9.9 – Device Inventory page
To access this view, follow these steps:
- Open a browser and navigate to https://security.microsoft.com.
- Click on Assets on the left side of the page.
- Select Devices.
The Defender portal also provides a configuration management dashboard that reports how endpoints and devices are managed, as shown in Figure 9.10:
Figure 9.10 – Configuration management dashboard
However, Intune is the recommended way to onboard. It can be leveraged to onboard Windows (except for servers), Android, and iOS/macOS devices. But first, Intune must be configured to connect with MDE.
Enable MDE in Intune and onboard devices
For specific instructions on enabling MDE within the Intune portal, see this page: https:// learn.microsoft.com/en-us/mem/intune/protect/advanced-threat-protection-configure
Then, onboard the organization’s supported devices to MDE. Use Intune to monitor the onboarding status and then set an MDE compliance policy. An MDE compliance policy is the level of acceptable risk for a managed device to be considered compliant. Risk classifications are set from the MDE perspective. So, once that is configured, if a device is classified as Clear or Low, it is considered compliant. But if a device is classified as Medium or High, it is marked noncompliant. Create app protection and Conditional Access policies to further determine devices’ compliance state.
When these configurations are set as per the organization’s policy, the two technologies (Intune and MDE) can work together to protect company data from an endpoint perspective. For example, when a device is marked as noncompliant, MDE will send an alert to the IT admin for further investigation. A Conditional Access policy will be applied to block the compromised device from accessing corporate data. MDE provides the capability to detect a compromised endpoint and protect malicious actors from trying to access company data.
Company data, including sensitive information, may live in Office 365 workloads such as Exchange Online mailboxes, Teams chats, and SharePoint Online files. You’ll next look at how Microsoft 365 Defender protects these workloads.

