Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps, or MDA (formerly Microsoft Cloud App Security, or MCAS), is a cloud access security broker (CASB) solution that can be connected to Office 365 and other SaaS applications to provide sophisticated analytics and security response actions. MDA is used to detect shadow IT applications in your environment, as well as evaluate risk factors for those applications. MDA is included as part of EMS E5.
When moving to the cloud, organizations need to find a way to secure their data and ensure adherence to company policies when users engage with these IaaS, SaaS, and PaaS services as well. A CASB addresses this by first discovering and monitoring users, apps, and data such as cloud traffic and company data. Then, IT or security admins can configure security and/or compliance policies per company or industry standards to protect users from cyber-attacks and compromise or prevent accidental or otherwise data leaks.
MDA has a framework made up of four main components:
- Identify and understand the usage of apps within the organization to curtail shadow IT. Shadow IT is the concept of users using apps that are either unknown by IT admins and/or have not been approved or sanctioned by the organization.
- Prevent data leaks. Identify, classify, and protect sensitive information from accidental or intentional exposure.
- Monitor and detect any unusual user behavior to curtail compromised identities, rogue apps, and otherwise potential cyber-attacks.
- Stay in compliance with cloud apps leveraged by the organization per industry standards.
Microsoft Defender for Cloud Apps best practices
Microsoft has published best practices for using MDA to protect the organization. These best practices contain guidance for the tasks that IT admins should perform regularly. They will help you understand the product much more deeply than the exam requires but will give insight as to the operations required to keep up with this service. Please see https://learn. microsoft.com/en-us/defender-cloud-apps/best-practices.
You will next look into how MDA’s features along with integrations with other applications and services work together to optimally address the framework.
First, to address the first part of the framework, IT admins must understand what apps are being used in the organization. To do this, MDA has a tool called Cloud Discovery. Cloud Discovery monitors the organization’s traffic logs and matches them against MDA’s inventory. MDA has an inventory of cloud apps that are organized by risk factors.
Cloud Discovery will then produce a report of its findings, for example, app categories such as productivity or CRM; risk levels that can be classified by high, medium, or low and can be customized; and discovered apps that may or may not be sanctioned. The dashboard will also present app users, IP addresses, the number of transactions and uploads, and more. Cloud Discovery can also produce reports and enhance the experience based on integrations. For example, an IT admin can choose to integrate with MDE to leverage machine-based analysis. Other integrations include Zscaler, a supported secure web gateway solution to seamlessly manage reports and configurations via the third-party tool directly.
Secure Web Gateway
To learn more about Secure Web Gateway, please visit https://www.secure-web-gateway.com/secure-web-gateway-zscaler/.
MDA helps protect sensitive data within the cloud, as per the second part of the framework. MDA accomplishes this by using Conditional Access App Control. This is a service that leverages an organization’s identity provider, or IdP, and its session and access controls. For the purposes of this exam, we will work with Azure AD and its Conditional Access features. Conditional Access is an Azure service that helps apply organizational policies based on data points such as users, locations, devices, applications, and risks. Based on organizational policies, IT admins can choose to block or grant access or require MFA based on an application, a user, their location, and more. If the organization is using Microsoft Purview and already has sensitive label policies set, MDA can integrate and use those rules to determine which data needs to be protected.
Conditional Access
Conditional Access is a tool that supports zero trust principles, as described in Chapter 7. This requires Azure AD Premium 1 licenses. For more information on Conditional Access, please see https://learn.microsoft.com/en-us/azure/active-directory/ conditional-access/overview.
With Conditional Access, Conditional Access App Control uses MDA’s services to interpret the signals generated when a user accesses data through a specific app. Granular policies can be applied further to specifically block access to or a specific action on sensitive data. So, to put all this together, for example, a corporate policy might call for a user in a specific group to be able to access sensitive data on a specific app such as Slack but only from a managed device within a specific IP range. Furthermore, the user, while accessing the data is allowed, will not be able to copy or send the data – MDA will block this in real time. IT admins can also use Conditional Access App Control to deploy a catalog of organization-approved apps.
The third part of MDA’s framework is to protect against any potential cyber threats and behavioral anomalies. To do this, as part of the published best practices, security admins need to stay vigilant in their monitoring and investigations. Security admins can do this through the Microsoft 365 Defender’s security portal. As part of MDA’s investigation tools, security admins can monitor activity logs, behaviors, activities, accounts, applications, and alerts.
Behaviors feature
MDA’s behaviors investigation, as of the time of writing, is in public preview. See here to learn more: https://learn.microsoft.com/en-us/defender-cloud-apps/ behaviors.
MDA, as a final part of its framework, is set up to help customers stay compliant with industry standards. HIPAA, NIST, CIS, and other industry standards have compliance requirements organizations need to follow. For example, a standard might require security admins to provide additional monitoring for admin accounts. MDA’s dashboard is used to collect and analyze information collected from these identities. Additionally, you can use the Cloud app catalog to help support that compliance requirement effort, as shown in Figure 9.15:
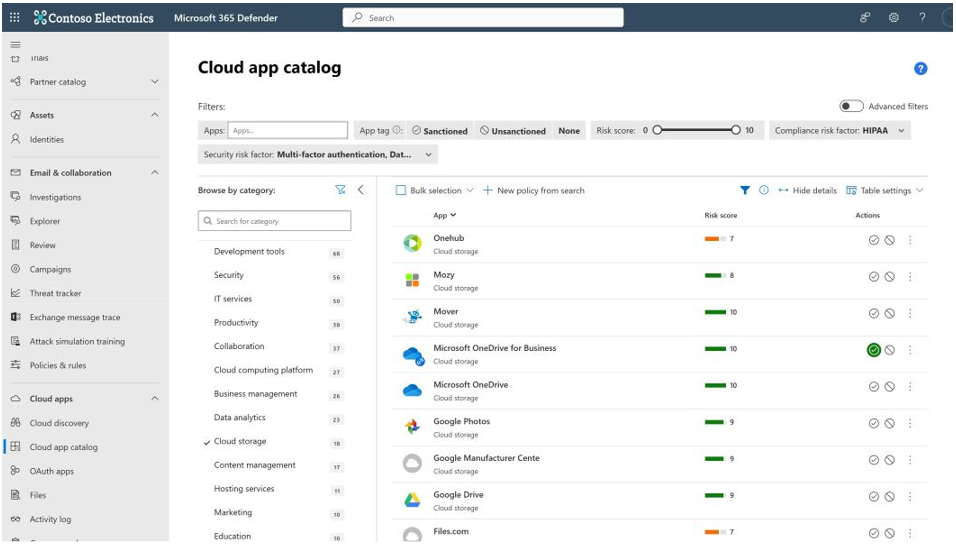
Figure 9.15 – Cloud app catalog
Figure 9.9, for example, lists cloud apps that take into consideration HIPAA’s compliance standards and the security risk factor associated with MFA and data classification. Each app has a risk score, and the Microsoft OneDrive for Business app is the only one in this example that has been sanctioned by the organization.
Figure 9.16 shows the Secure Score recommendations for cloud apps that adhere to the MDA framework:
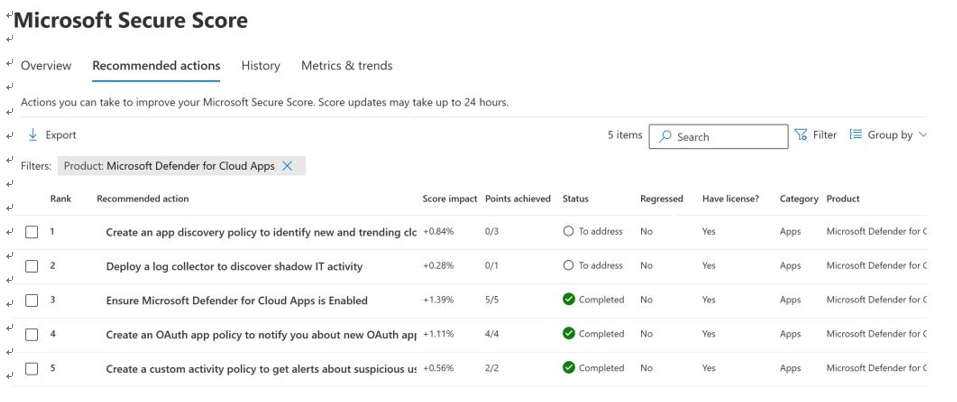
Figure 9.16 – Secure Score recommendations for Cloud Apps
For example, one of the recommended actions displayed in Figure 9.10 is for admins to set up a log collector to address the first part of the framework—discover shadow IT.
MDA collects a lot of information pertaining to incidents and alerts. To manage these, security administrators can choose to integrate with Microsoft Sentinel.
MDA integration with Microsoft Sentinel
As of the time of writing, MDA’s integration with Microsoft Sentinel is in public preview. To learn more, please see https://learn.microsoft.com/en-us/defender-cloud-apps/siem-sentinel.
Next, you’ll take a deeper look at Microsoft Secure Score.

