Describe the Purpose and Value of Implementing Entra ID Features
Once you have chosen an identity and an authentication model, you should think about securing the identity in question as well as how to handle common end-user management tasks such as password reset.
In this section, you will learn about multi-factor authentication—one of the tools available to all users of the Microsoft 365 platform for securing identities and logons.
Multi-Factor Authentication (MFA)
Users typically provide login credentials (usually a username and a password) for most authentication or login attempts. The methods of authenticating a user’s identity typically fall into one of the following three categories:
- Something the user knows: A password is the most common example of this method.
- Something the user has: This can be some kind of login device, such as a smart card or token, or it can be a text or phone call to a phone number previously registered with the system that the user is attempting to access.
- Something the user is: With this method, the user must supply some sort of biometric input, such as a fingerprint, iris scan, or voice passcode.
There are a lot of scenarios, however, where a simple username and password may not be enough to secure valuable resources. In such cases, organizations may wish to further challenge a user during the login process to verify their identity. MFA provides this ability by introducing one or more challenges to the user during the authentication process.
Azure AD has a native MFA service that can be used to further protect users and administrators and can be easily enabled. Azure AD MFA currently incorporates the following options for further authenticating users:
- SMS or text message
- Phone call
- One-time passcode on a hardware or software token
- Confirmation prompt on a registered authentication app
MFA has several features, such as self-service secure registration or the ability for users to bypass MFA if they are connecting from secure, known networks. More in-depth information about the configuration capabilities of Azure AD MFA, including steps to configure third-party tokens for verification, can be found at https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-howitworks.
Entra ID provides several different identity and authentication models, as well as security controls, to provide a strong level of protection for your organization. Implementing Conditional Access and MFA can help organizations verify that users who are presenting credentials and attempting to obtain access to resources are authorized to do so and are using compliant devices.
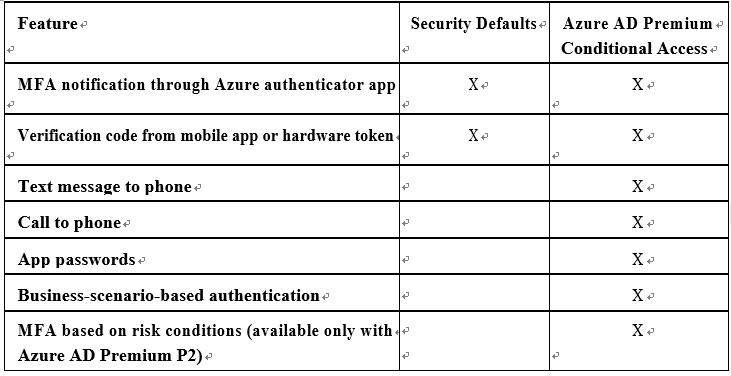
MFA is available via several mechanisms in Microsoft 365. All plans are eligible for basic MFA using a feature known as security defaults. This basic MFA option does not provide much granularity, and it has fewer authentication options than the Conditional Access features offered through the Azure AD Premium P1 or P2 licenses.
Table 8.2 outlines the capabilities and features of security defaults and Conditional Access, available as part of an Azure AD Premium license:
Next, you’ll explore some of the concepts involved in the self-service password reset process.

