Describe How Microsoft 365 Addresses the Most Common Threats
Microsoft 365 Defender’s suite of security services is designed to help mitigate attacks like this by monitoring, detecting, and alerting—as well as taking automated remediation steps.
MDO and EOP analyze messages as they come through your environment. Together, MDO and EOP can detect advanced threats, including malicious links, attachments that have malware containing time-based activation, and phishing attempts in addition to traditional viruses and spam.
MDE is constantly monitoring devices for anomalous behavior, such as applications that attempt to execute macros, or scripts or code that connect to external websites. MDE also allows security analysts to isolate devices on the network—preventing them from contacting other devices.
Microsoft 365 Defender’s incident response and alerting feature allows you to see threats and risks through the environment and take actions to classify events, lock out identities, and block devices from accessing other network resources. Figure 9.20 depicts the Microsoft 365 incident management page, providing detailed information about suspicious activity.
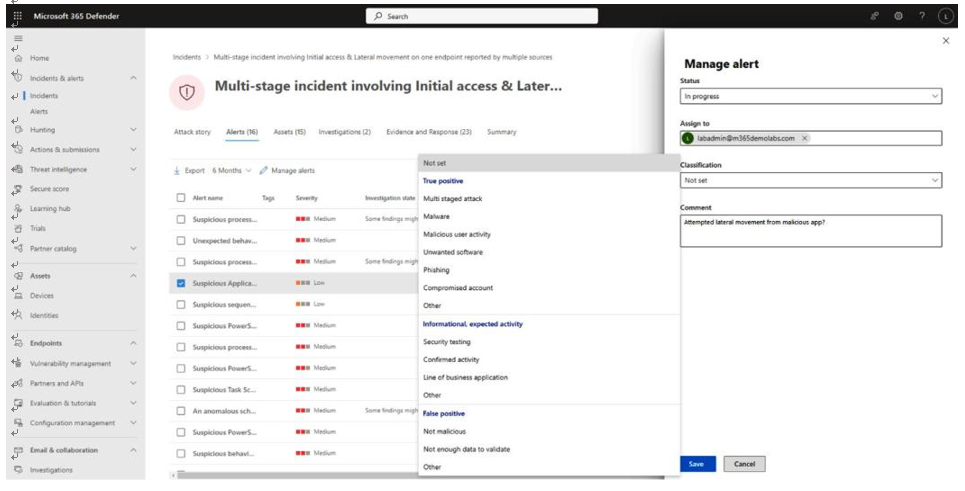
Figure 9.20 – Microsoft 365 Defender incident management
With automated investigation and response (AIR), Defender can take actions such as forcing a user to re-authenticate using MFA, isolating devices, and quarantining suspected malicious files.
From a proactive perspective, Microsoft Defender also includes tools such as attack simulation training, allowing you to run phishing campaigns against users to help train them in identifying and reporting risks.
Together, this suite of security services can help safeguard an organization’s environment.

