Describe auditing and eDiscovery solutions
Sometimes, organizational operations will require proof that they are complying with certain industry regulations or legal rulings. Or, they may have to open an investigation into actions taken by a threat actor. The auditing and eDiscovery capabilities of Microsoft 365 can be used to fulfill these types of requests.
Audit
Compliance has been defined as being able to prove policy. One of the ways you can prove actions is through logs. In the Microsoft 365 platform, nearly every conceivable action generates some form of logging event—whether it’s signing in to the service, completing an MFA challenge, connecting to a mailbox, modifying permissions to a file stored in SharePoint, adding or removing a group member, resetting an account password, or creating a transport rule in Exchange Online.
These events are collected inside the Microsoft 365 Audit log, shown in Figure 10.13:
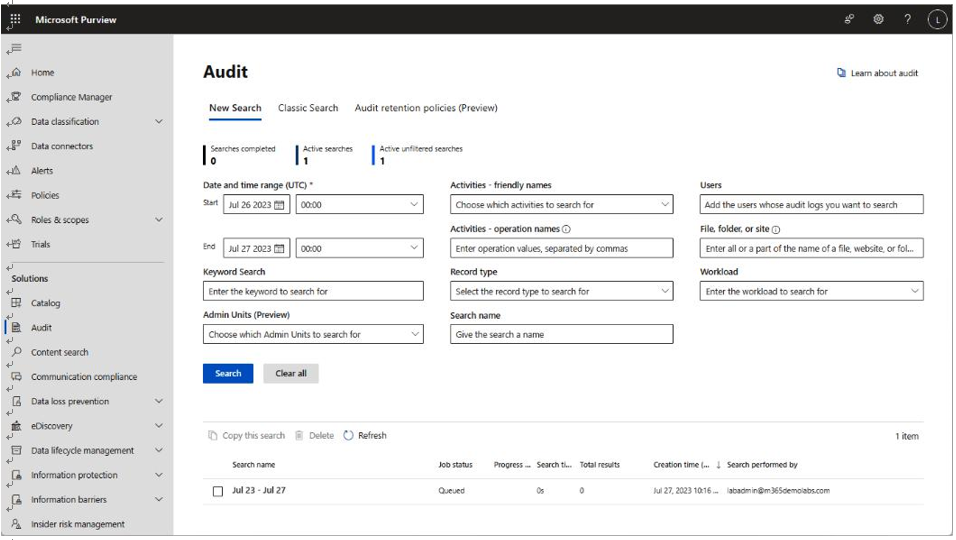
Figure 10.13 – Microsoft Purview Audit log
The Audit log provides visibility into events generated by users or other service principals in Azure AD, Exchange Online, SharePoint Online, Viva Engage (or Yammer), Cloud App Security, Microsoft 365 Defender, eDiscovery search, Microsoft Forms, and more. When searching the audit log, you can filter using the following options:
- Date and time range: This parameter allows you to specify a start and end time frame. Dates are stored in UTC format, so you’ll need to add or subtract hours based on your time zone offset.
• Keyword search: This parameter lets you search events for specific words or phrases.
- Administrative units: You can scope the audit search to just objects in particular administrative units (styled as Admin Units in the search interface).
- Activity types: You can query for the different types of activities (typically CRUD, or Create, Read, Update, and Delete), either by a friendly name (such as Accessed a file or Changed record status to locked) or the actual operation name as it’s stored in the log (such as UpdatedUserBriefingSettings or ExtendRetention).
- Record type: This is closely related to theWorkload property and indicates the service or feature operation that triggered the record.
- Users: The Users field is used to filter records by the user performing the activity (sometimes referred to as the actor).
- File, folder, or site: For content-related audit logs, this location property can be used to limit the scope of the search to individual content paths or document names.
- Workload: Closely related to Record type, Workload is used to identify the Microsoft 365 service where the audit entry was generated.
When reviewing the results of a search, as shown in Figure 10.14, you select an individual item to view the details of the particular entry:
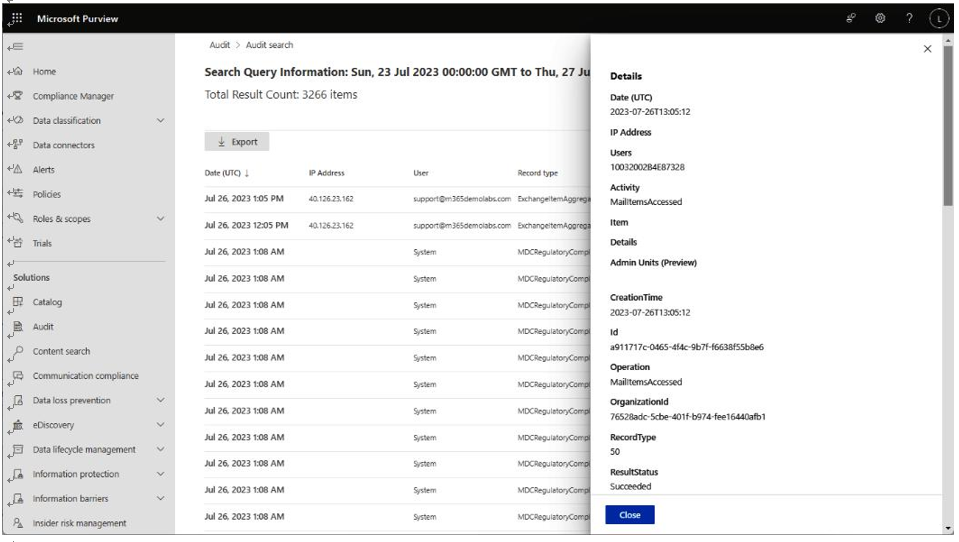
Figure 10.14 – Viewing an individual audit log
The type of detail displayed will depend on the type of entry being viewed. You can also further refine the output using filters. The Export button allows you to generate a CSV containing the matching records.
Depending on your Microsoft 365 licensing, audit logs may be retained for different periods of time. By default, Microsoft 365 retains all log data for 90 days for users who are assigned any Office 365 or Microsoft 365 license besides A5, E5, or G5. For users that have been assigned an Office 365 A5, E5, or G5 license, a Microsoft A5, E5, or G5 license, a Microsoft 365 E5 Compliance license, or a Microsoft 365 E5 eDiscovery and Audit add-on license, logs are automatically retained for a year. The premium licenses also allow organizations to create up to 50 custom audit retention log policies, which can be used to preserve log data for up to 10 years.

